Table of contents:
The process of remote device management is usually described by a model that consists of seven stages: from device provisioning to software maintenance and updates. Below, the 2Smart team shows how these steps are implemented in practice in the business platform it has developed for managing a chain of devices.
Briefly About What is the 2Smart Business Platform
A business platform is a tool for companies that use the Internet of Things devices in their processes, which is a remote device management software. IoT devices can be the backbone of such companies’ business, for example, if they provide consumer services through connected devices. Or IoT devices can be ancillary equipment for manufacturing, agricultural, and other companies.
Whichever category of the two described above a company belongs to, it needs a tool for remote management of IoT devices, which is a business platform. Using this automation framework, a business can manage users, their roles, companies, and participations, that is, the roles of specific users in specific companies.
Of course, the business panel also allows you to manage remote IoT device, which is described below.
7 Steps for Remote Management of Devices
1. Provisioning
In theory: This step involves preparing the IoT device for deployment by assigning a unique identifier, such as a serial number, to the device. The device is also given a set of initial settings, such as default usernames and passwords, to enable secure communication with the cloud or other remote device management tools.
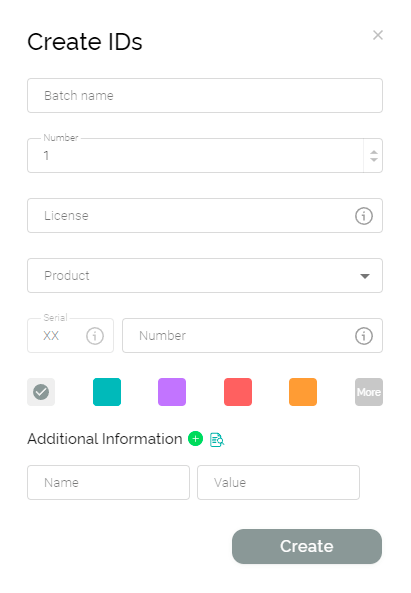
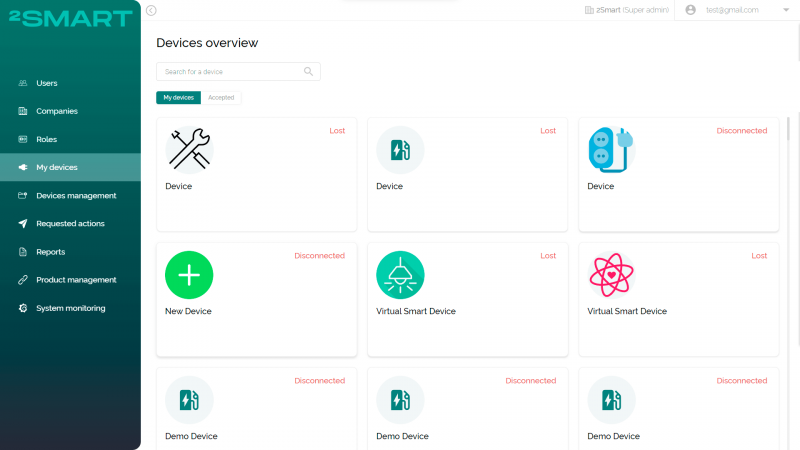
How it works in practice in 2Smart: In the 2Smart business panel, provisioning a batch of IoT devices begins with assigning them identifiers called Device IDs. The system administrator generates the required number of identifiers. For the convenience of IDs management, they also specify such parameters as batch name, the number of identifiers to be generated, and any additional info. To visually distinguish this group of identifiers in the general list in the business panel, the administrator can also select the color with which they will be marked.
In addition to each identifier, the remote device management system automatically generates an image file with a QR code corresponding to the Device ID. The generated identifiers and QR codes are available in the business panel and must be assigned to physical devices.
To do this, IoT devices must be flashed so that the firmware code contains the ID of this instance. 2Smart business panel provides two options:
- The administrator downloads a batch of QR codes and a .csv file with Device IDs and other information for the entire batch of devices and sends them to the device manufacturer. The manufacturer flashes the devices and places the ID on the device case and/or in the accompanying documentation in text form or as a QR code.
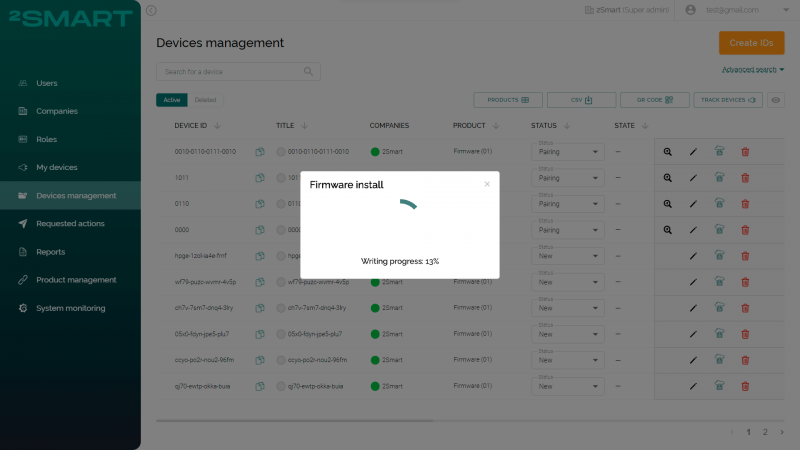
- The administrator manually installs the firmware on the devices by connecting them one by one to the computer using a USB cable. The firmware is installed from a browser through the web interface of the business panel. No additional software and the ability to use it is required, so any without special skills can do this.
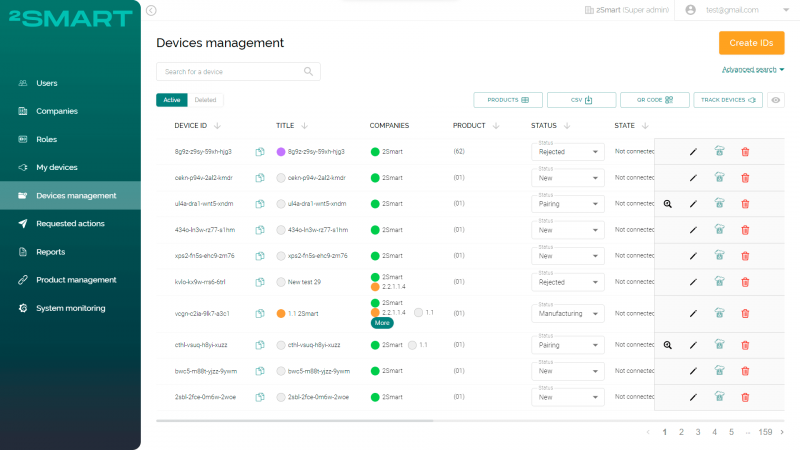
Each device added to the business panel has a certain status, depending on the stage at which the Device ID assigned to it is. There are three statuses used in the Provisioning step:
- “New” – Device ID is generated (in a single copy or as part of a batch).
- “Manufacturing” – the device is in the process of production and not ready to use.
- “Manufactured” – the device production is finished; it is flashed with firmware with Device ID in the code and is ready for pairing by the end user.
The status switches from “Manufacturing” to “Manufactured” automatically if the device manufacturer uses the 2Smart remote device management service API. Also, an administrator can switch this status manually.
2. Identification authentication
In theory: Authentication is a crucial step in the functioning of IoT systems, as it involves verifying the identity of devices that join the network to prevent unauthorized access and maintain the confidentiality of sensitive information. Administrators must establish robust device and network security settings that can authorize or deny access attempts to enable authentication. While the authentication process may vary depending on the device, each device comes with a unique certificate or key that validates its identity. Credentials such as model and serial numbers are commonly used to verify the device’s identity.
How it works in practice in 2Smart: Assigning a unique identifier to each device instance is precisely the preparation for the identification authentication stage. The security assessment framework of the 2Smart Cloud business panel uses a classical approach of creating a whitelist. A specific set of privileges attaches to each device (MCU) in the system, with the supervision and final approval from the administrator, allowing them to perform only actions that are explicitly allowed to a particular subject.
The device in the identification authentication step can have one of the following three statuses in the business panel:
- “Free” – the device with this Device ID is ready for transfer to the end user or has already been transferred to them and is waiting for pairing.
- “Pairing” – the user is pairing the device. The system checks the compatibility of the user, device, company, and other parameters; that is, authentication is performed on the remote device management system side.
- “Paired” – the user has paired the device.
Usually, the “Paired” status is the last one in the chain of device statuses. It means that the user successfully utilizes the device, and all the stages of remote management of IoT devices listed below are relevant for the paired device.
3. Configuration
In theory: Once a new device is installed, a further configuration can be carried out after the initial setup phase. This may involve adding more complexity and intelligence to the device, enhancing its functionality with additional code, or adjusting its settings to meet new requirements.
How it works in practice in 2Smart: After the pairing is completed, the device user can configure all the parameters of its operation using the mobile application. Configuration can also be performed by the system administrator using the remote device management service interface, where they have access to manage a specific connected device (more on this in the next section on device control).
In addition, the firmware of 2Smart Cloud devices provides a reserve configuration option in the form of a built-in admin panel. The user or administrator can use it if there is no way to work through the cloud-based environment or the device is disconnected from the Internet.
4. Control
In theory: Once the device is configured, remote control of the device is possible. This enables the device to be turned on/off or its settings to be changed from a remote location.
How it works in practice in 2Smart: Device control in 2Smart remote device management service can be carried out both on the side of the end user and on the side of the system administrator or serviceman.
Control by the end user
The end user mainly controls the device via the mobile app. It can be a native 2Smart Cloud application or its white label version, branded for the system customer; it doesn’t matter.
In addition to the app, the end user can utilize such device control methods as voice commands, free phone calls, iPhone shortcuts, etc.
The user can also log in to the 2Smart business panel in browser, where they can control devices using a mobile application emulator.
Control by the admin
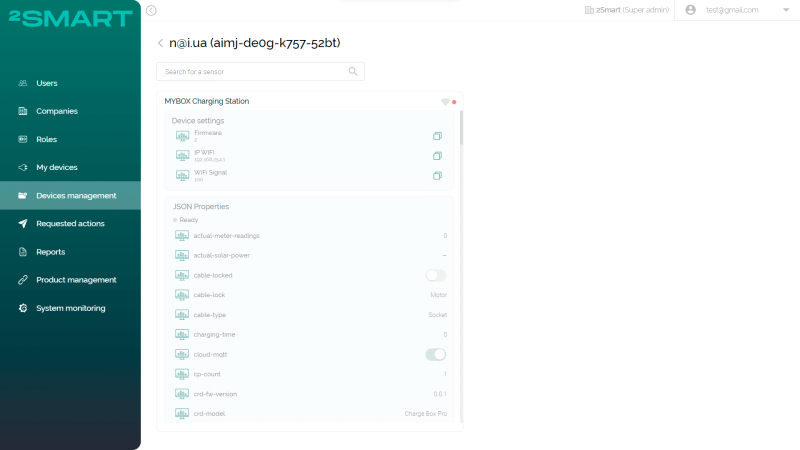
The system administrator or serviceman also has access to a particular device, knowing its identifier. The web interface of the business panel allows them to open a page that contains a list of all device sensors and their current values received from the MQTT broker. If the sensor implies the ability to change the value (for example, it is a logical sensor), and the device is online, the administrator can remotely change the state of the sensor.
In addition, the end user can set up sharing of their device for the serviceman, allowing him to manage remote IoT device using a mobile application on his smartphone or tablet.
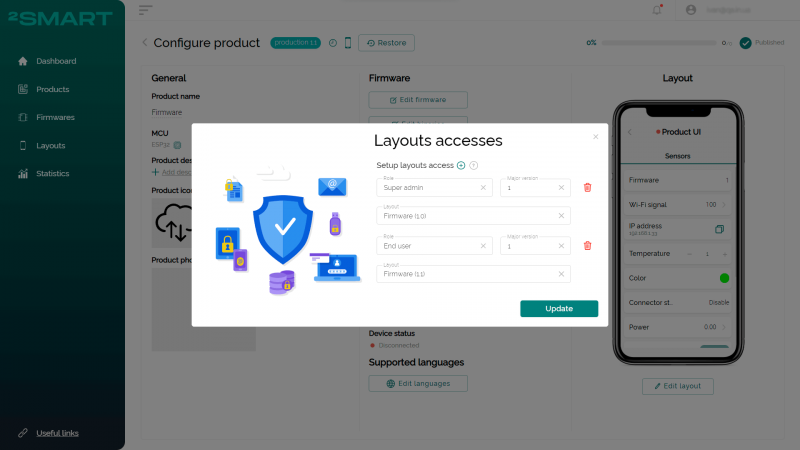
By the way, the 2Smart remote device management platform allows you to customize the mobile application interface differently for users with different roles. For example, the end user may only have access to the widgets that control the device, while the serviceman may receive complete telemetry.
The layout access functionality is another business opportunity for companies using the 2Smart centralized remote device management platform. They can offer users different models of using the application when extended functionality in the form of access to extra widgets can be available for an additional fee.
Disclaimer
Recall that the 2Smart business panel is designed for remote management of IoT devices that belong to companies. For example, it operates a chain of EV charging stations. Therefore, the possibility of administrator intervention in the operation of the device does not violate the end user’s privacy, as could be the case with privately-owned remote devices.
5. Monitoring
In theory: It’s important to monitor the device to ensure it is functioning properly and to detect any potential issues. This involves collecting data from the device, analyzing it, and sending alerts to the appropriate personnel when anomalies or errors are detected.
How it works in practice in 2Smart: System administrators can monitor device usage, control the status of each instance in real-time, configure it, and receive notifications from it.
Also, to monitor the system as a whole, the Grafana web application is connected to the 2Smart business panel, which allows you to visualize data on dashboards using charts, graphs, and tables. Grafana also allows you to set alerts for events that could potentially indicate the possibility of serious system failures, data loss, or performance degradation.
6. Diagnostics
In theory: If an issue is detected, remote diagnostics can be performed to determine the root cause without physically visiting each device installation point. This can involve remotely accessing the device’s logs or running diagnostic tests.
How it works in practice in 2Smart: The functionality described above for accessing device telemetry using the 2Smart business panel allows for its remote diagnostics. Since the administrator sees a complete list of sensors of any device, as well as a history of their status, in many cases, they can manage issues with remote devices.
We also described the opportunity of sharing a device with a serviceman. Having access to telemetry widgets that are inaccessible to the average user, a technician can not only control the device from their hybrid workplace but also perform diagnostics without access to the business panel.
7. Software Maintenance & Updates
In theory: Software maintenance and updates are necessary to keep the device running smoothly and securely. This involves remotely updating the device’s firmware, security patches, and other software components. These updates can be done manually or automatically, depending on the device and organization’s policies.
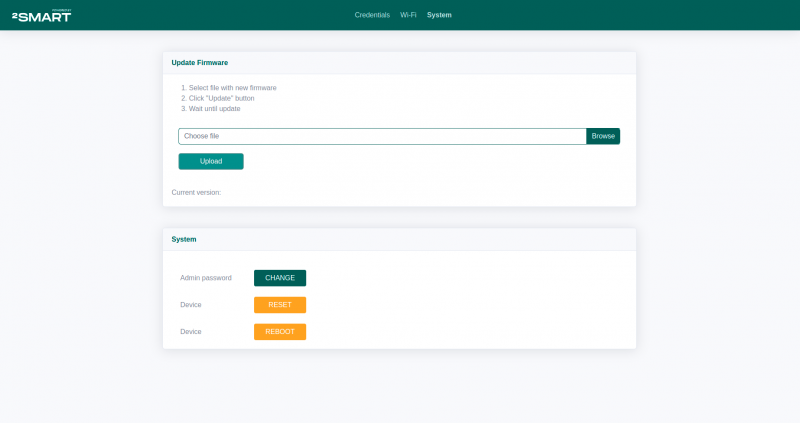
How it works in practice in 2Smart: The primary way to update the firmware of devices connected to the 2Smart Business Panel is over the air (OTA). To update the entire batch of connected devices, the administrator or technical specialists of the company upload the updated firmware file using the interface of the 2Smart Cloud developer panel (the flow of how to do it is described in our article on how to add your effect for a Wi-Fi lamp).
Each device instance is configured to specify whether it should receive updates automatically (and at what time of day) or whether updates can only be manually installed by an administrator. Manual update means that the administrator needs to start the update process from the business panel or mobile application using the widget designed for this.
If technicians need to test a new firmware version on a limited number of devices, they can use the staging mechanism.
What is the result
As you can see, remote device management in practice looks much more diverse than in the strict framework of the theory. Developers can apply unique solutions and implement additional features for business at each stage of this process. If you are interested in the 2Smart remote device management solutions, smart home automation solutions, and others, feel free to write us a request for its demo at contact@2smart.com.
FAQ
Is it secure to operate IoT devices remotely?
With proper security measures in place, operating IoT devices remotely can be a secure and effective way to manage and control these devices from a distance.
What are the benefits of enabling IoT devices to communicate remotely?
Enabling IoT devices to communicate remotely can improve device management, increase efficiency, and provide organizations with a more comprehensive understanding of device performance and usage.
What are some best practices for effective remote device management in IoT, particularly when operating and communicating with devices remotely?
Some best practices for effective remote device management in IoT include standardizing device communication protocols, implementing security measures to protect against cyber threats, using the right technology of device management, utilizing cloud-based platforms for enterprise IoT device management, and implementing machine learning algorithms for predictive maintenance.
Don't forget to share this post!
Read Next
Let’s dive into your case
Share with us your business idea and expectations about the software or additional services.