Table of contents:
In an increasingly connected world, securing embedded devices is paramount to protect sensitive data, ensure device integrity, and prevent unauthorized access. Espressif’s IoT Development Framework (ESP-IDF) offers robust tools and features to bolster firmware security on ESP32 and similar microcontrollers. This article delves into critical security-enhanced firmware techniques using ESP-IDF, focusing on encrypted flash, secure boot, additional security improvements that developers can implement to safeguard their devices, and how the 2Smart team can help you with this task.
Introduction to Firmware Security
Firmware, as the fundamental layer of software for hardware devices, plays a critical role in both functionality and security. Because firmware operates so closely with hardware, vulnerabilities at this level can serve as entry points for malicious attacks, enabling unauthorized access, system manipulation, and data theft. With the increasing reliance on IoT devices, ensuring firmware security is no longer optional — it’s a necessity.
In this context, Espressif’s IoT Development Framework (ESP-IDF) provides a comprehensive set of security tools designed to protect the firmware on Espressif microcontrollers. The ESP-IDF simplifies the implementation of advanced security features like encrypted flash storage and secure boot, ensuring that only trusted firmware versions are executed and sensitive data remains protected. These tools, combined with best practices, help create a secure development environment, enhancing device resilience against a range of cyber threats.
This article will explore two key features of ESP-IDF: encrypted flash and secure boot. We’ll also explore other firmware security strategies to fortify IoT devices and reduce potential attack vectors. Whether you’re new to firmware security or looking to strengthen your existing IoT solutions, these techniques will guide you toward building more resilient devices.
Encrypted Flash in ESP-IDF
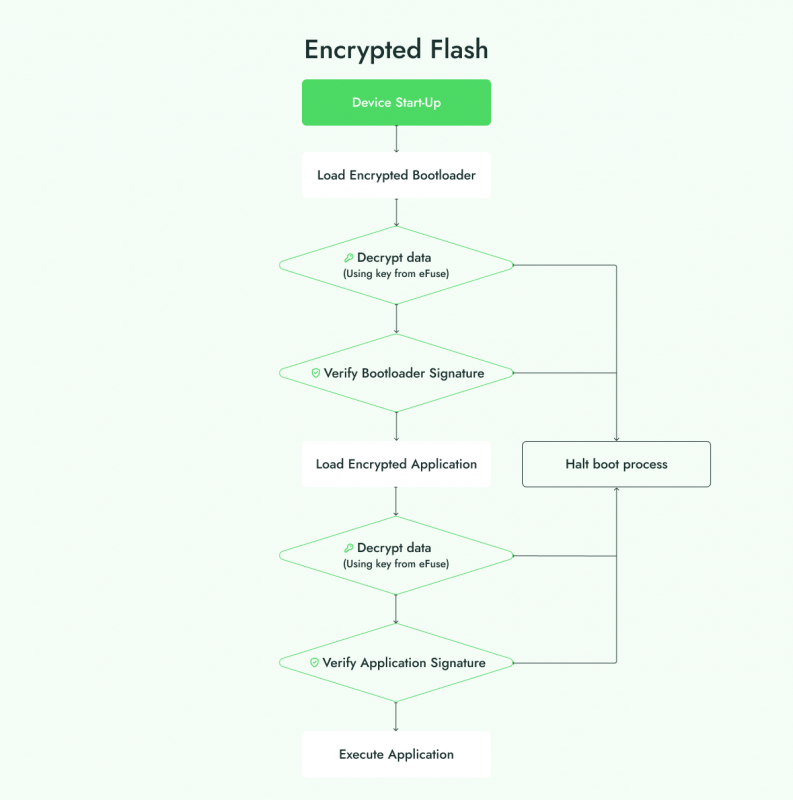
Securing firmware data on IoT devices is vital to protect against unauthorized access and manipulation, especially in cases where physical access to the device is possible. One of the key security features in ESP-IDF for safeguarding firmware is encrypted flash. This process uses AES (Advanced Encryption Standard) encryption to lock down the contents of the flash memory, ensuring that firmware data is automatically encrypted when written and decrypted when read. Encrypted flash significantly increases the difficulty for attackers attempting to extract or reverse-engineer sensitive information from the device by making the firmware inaccessible without the decryption key.
Advantages and Disadvantages of Encrypted Flash
Implementing encrypted flash on ESP-IDF brings notable benefits, but also some trade-offs. Here’s a closer look at both sides:
Advantages:
- Data confidentiality: With encryption, firmware is unreadable without proper decryption keys, which protects the code from unauthorized access and tampering.
- Integrity assurance: Encrypted flash verifies the integrity of firmware, making it clear if any alterations were made, as changes invalidate the encryption.
- Regulatory compliance: Many industry standards mandate data protection. Encrypted flash supports compliance with these requirements by securing stored firmware data.
- Defense against reverse engineering: Encryption makes it much harder for attackers to decode the firmware’s structure, protecting the device from reverse engineering attempts.
Disadvantages:
- Performance overhead: Encryption and decryption processes add computational load, potentially impacting device performance, particularly in resource-constrained microcontrollers.
- Complex key management: Securely handling encryption keys is crucial yet challenging, as it requires robust storage and protection methods.
- Reduced debugging flexibility: Encryption complicates debugging since firmware data cannot be directly accessed or altered during development.
- Increased power consumption: For battery-operated devices, the additional power consumed by encryption can be a significant drawback.
How the device boots with an Encrypted flash feature
Restrictions and Considerations
Encrypted flash in ESP-IDF also comes with certain limitations based on the specific use case. For instance, when using SPIFFS (SPI Flash File System) — a common storage system for files on ESP devices — encryption introduces additional constraints:
- File size limits: Encrypted SPIFFS may have restrictions on the maximum file size it can handle effectively.
- Performance impact: The on-the-fly encryption and decryption in SPIFFS can slow down file access times, adding latency to read/write operations.
- Compatibility: Ensuring SPIFFS compatibility with encryption is essential to avoid data corruption or access issues.
Lastly, consider the hardware constraints associated with encrypted flash. For example, the flash memory size may be effectively reduced due to the storage needed for encryption metadata, and devices with limited CPU power may struggle to handle the computational demands of encryption smoothly. These factors must be evaluated to determine if encrypted flash is feasible and practical for a given IoT application.
Secure Boot Mechanism
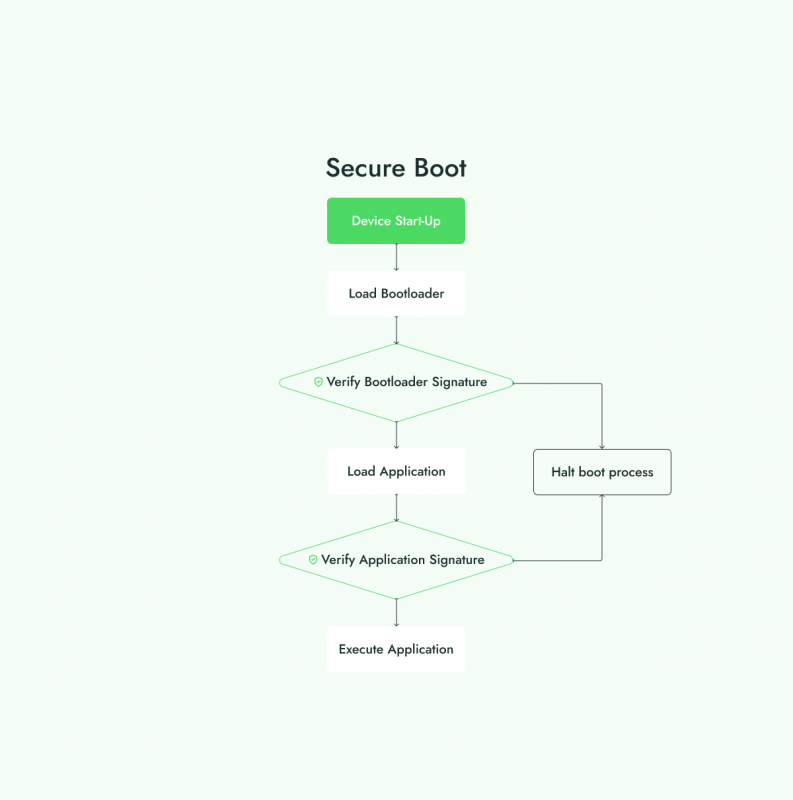
As devices become increasingly connected, the security of their firmware is paramount. Secure Boot is a critical security measure within ESP-IDF designed to protect the device from unauthorized or tampered firmware. By ensuring that only signed and verified firmware can execute, Secure Boot mitigates the risk of malware or unauthorized code being loaded onto the device. This mechanism works by verifying the firmware’s digital signature each time the device boots. If the signature does not match the stored public key, the device halts the boot process, effectively blocking any unapproved code from running.
In ESP-IDF, developers can implement Secure Boot using RSA or ECDSA (Elliptic Curve Digital Signature Algorithm), both of which provide strong security for authenticating firmware. When Secure Boot is enabled, the public key is embedded in the bootloader and used to check the digital signature of the firmware, verifying its authenticity before loading it into memory.
Benefits of Secure Boot
Implementing Secure Boot offers multiple security advantages that protect both the device and its users:
- Protection against unauthorized firmware: Secure Boot ensures that only authorized firmware versions are installed and executed. This effectively blocks attackers from flashing or running tampered firmware on the device, strengthening overall system security.
- Maintains device integrity: By allowing only verified firmware to execute, Secure Boot maintains the device’s integrity, preventing any alterations that could compromise performance or open security vulnerabilities.
- Establishes trust: Secure Boot creates a foundational trust between the device hardware and its software, building a “chain of trust” that strengthens the device’s security posture across its entire lifecycle.
- Meets regulatory compliance: For applications in highly regulated industries like healthcare, finance, and industrial automation, Secure Boot helps meet strict security standards, making the device compliant with data protection and cybersecurity regulations.
These benefits make Secure Boot an essential component of firmware security, helping to ensure that devices remain protected from unauthorized access and potential cyber threats at a foundational level.
How the device boots with a Secure Boot feature
Advanced Firmware Security Strategies Recommended by the 2Smart Team
In addition to foundational protections like encrypted flash and secure boot, developers can further strengthen device security by limiting physical access points and tightening firmware management. The 2Smart team suggests two additional techniques: disabling UART logging and restricting USB-based firmware flashing. These strategies help safeguard devices in production environments by reducing access points for potential attackers.
Disabling UART Logging for Production
UART (Universal Asynchronous Receiver-Transmitter) logging is often crucial during development, enabling developers to track system states and diagnose errors. However, in a production environment, leaving UART logging enabled can expose sensitive information — such as system errors, state changes, or cryptographic details — to anyone with physical access to the device.
Implementation Strategies
1. Disable UART logging in production builds:
- Configure ESP-IDF to turn off all debug logs and UART output when generating production firmware.
- This can be achieved by setting the log level to
"NONE” in thesdkconfigfile:CONFIG_LOG_DEFAULT_LEVEL_NONE=y
2. Conditional access through Development mode:
- Implement a dual-mode setup where the device runs in a secure mode with UART logging disabled by default. Provide an option to activate development mode for authorized personnel, enabling UART logging only when needed for troubleshooting.
- Restrict this mode change through secure authentication (e.g., digital certificates or secure tokens), ensuring that only approved users can access sensitive log data.
Benefits of Disabling UART Logging
- Enhanced data protection: Reduces the risk of sensitive information leakage through open UART interfaces.
- Operational flexibility: Allows for secure debugging access without compromising device security under normal conditions.
Preventing Unauthorized USB Firmware Flashing
USB-based firmware flashing is useful for updates and maintenance, but it can be a vulnerability in production devices. If USB flashing remains enabled, unauthorized individuals could potentially install malicious firmware, compromising device integrity.
Implementation Strategies
1. Disable USB flashing for production firmware:
Configure the production firmware to disable the bootloader’s USB flashing capability post-deployment. This can involve physically disabling or removing the USB interface used for flashing, or setting bootloader locks to block unauthorized reprogramming.
2. Implement authentication mechanisms for USB flashing:
Require authentication for USB-based firmware updates. Use secure methods such as digital signatures or encrypted tokens, ensuring that only verified firmware is allowed to be flashed onto the device.
Benefits of Restricting USB Flashing
- Prevents malicious firmware installation: Blocks unauthorized access and protects against the installation of tampered firmware.
- Ensures firmware integrity: By controlling USB access, only trusted, verified firmware versions can be installed, safeguarding the device’s functionality and security.
These additional security enhancements, when combined with encrypted flash and secure boot, form a robust multi-layered defense against unauthorized access and firmware tampering, ensuring that devices remain secure across various deployment environments.
Best Practices for Strengthening Firmware Security
Implementing effective firmware security with ESP-IDF requires not only applying specific features like encrypted flash and secure boot but also following structured best practices. These practices help developers maximize device protection, reduce vulnerabilities, and ensure long-term security. Here are the essential guidelines for securing firmware in ESP-based devices.
Secure Key Management
Proper key management is foundational for any security framework. To prevent attackers from obtaining sensitive encryption keys or digital signatures, storage should be handled with caution.
- Use hardware-based security modules: Store encryption keys and other sensitive data in secure hardware components, like the ESP32’s eFuse, which provides physical protection and prevents key extraction.
- Avoid hardcoding keys: Embedding keys directly in firmware makes them accessible to anyone with reverse-engineering capabilities. Instead, manage keys in secure, external hardware to ensure they remain protected from unauthorized access.
Conduct Regular Security Audits
Even the most well-implemented security measures require routine checks to maintain effectiveness. Regular security audits help developers identify and fix vulnerabilities before they can be exploited.
- Periodic reviews and assessments: Conduct security assessments at every stage of the development cycle and periodically after deployment. This helps detect any configuration issues or coding flaws that could expose vulnerabilities.
- Stay updated with Espressif’s security patches: Keeping firmware and security features up-to-date is crucial. Espressif periodically releases security patches that address newly identified vulnerabilities; applying these patches is an essential part of proactive device management.
Minimize the Device’s Attack Surface
Reducing the number of active components and accessible services on a device minimizes the points at which an attacker can gain access.
- Disable unused peripherals and services: Turn off any hardware peripherals, services, or interfaces not essential to the device’s core functions. This simple step can close off several potential attack vectors.
- Apply the principle of least privilege: Ensure each system component or module has only the permissions necessary to perform its tasks, reducing the risk of an exploited component affecting the entire system.
Implement Secure Firmware Updates
Firmware updates, though essential, can introduce security risks if not managed correctly. Secure update mechanisms ensure that devices only install authorized and verified firmware.
- Use encrypted and signed OTA updates: Over-the-air (OTA) updates should be both encrypted and digitally signed. Encryption prevents unauthorized access to firmware data, while signatures verify authenticity and guard against tampering.
- Verify firmware integrity: Before applying any update, verify the integrity and authenticity of the firmware package. This step ensures that only legitimate updates are installed, maintaining the device’s operational security.
Following these best practices helps to create a layered security approach that protects ESP-based devices from a range of potential threats, making them resilient and reliable across various environments. By adhering to these practices, developers can leverage ESP-IDF’s security features to their fullest potential, ensuring both data and device integrity.
Conclusion
Securing firmware is essential for creating robust, dependable IoT devices, as firmware lies at the core of device functionality and security. ESP-IDF provides developers with fundamental tools like encrypted flash and secure boot, which safeguard devices from unauthorized access, reverse engineering, and tampering. These primary security measures play a critical role in ensuring that firmware remains confidential and unaltered, building a trusted foundation for embedded systems.
Yet, implementing these security features involves a careful balance. Techniques like encrypted flash and secure boot enhance device security but introduce additional complexity in development and deployment. Missteps in configuring encryption or key management could render devices inoperable, while each security measure requires responsible key storage and maintenance. Furthermore, additional strategies — like disabling UART logging and restricting USB flashing — add crucial layers to device security by further minimizing potential attack vectors, even though they can also complicate debugging and firmware updates.
At 2Smart, we’ve examined both the benefits and challenges of these security approaches. To address the complexity and streamline the secure delivery process, our team is developing a comprehensive solution that meets these rigorous security standards. This system is designed to manage secure OTA firmware updates, provide centralized storage for secure boot and encryption keys, and handle version control to ensure seamless and trustworthy device updates. With this approach, we aim to equip developers with a powerful framework for secure firmware management, enabling IoT devices that are both reliable and resilient in the face of evolving security threats.
Don't forget to share this post!
Read Next
Let’s dive into your case
Share with us your business idea and expectations about the software or additional services.