Table of contents:
At 2Smart, we leverage bastion servers to control access between our services and the white-label instances of the 2Smart platform, ensuring a secure, scalable, and robust IoT environment. As our platform continues to grow and evolve, we’ve implemented best practices to safeguard our infrastructure against the increasing complexity of cyber threats. In this article, we’re sharing our team’s experience using bastion servers to secure our services, offering insights and recommendations for anyone looking to strengthen their IoT network security.
What is a Bastion Server?
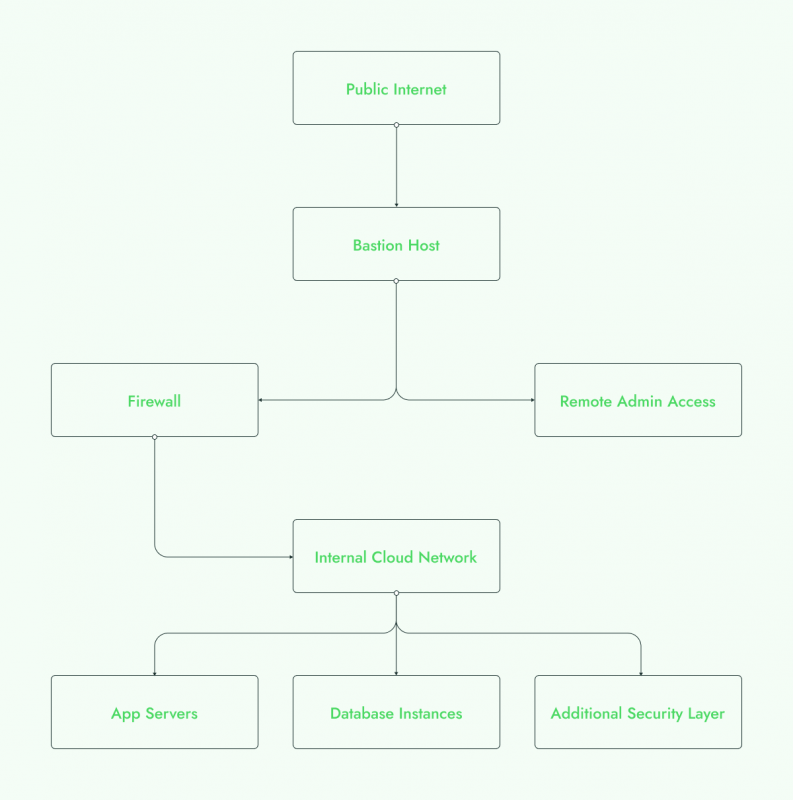
A bastion server, or bastion host, is a highly secured server positioned at the network perimeter. It acts as a gatekeeper between external networks (such as the Internet) and the internal network, controlling access to sensitive systems. By focusing its resources on security, a bastion server is designed to withstand direct attacks while limiting exposure to internal systems.
Bastion servers typically offer SSH or RDP access to critical infrastructure and employ stringent authentication methods. Their design includes minimal open services, and they’re regularly updated to prevent vulnerabilities. In a production IoT environment, where many devices may lack robust security, the bastion server ensures that only authenticated users can gain access to sensitive areas of the network.
Why Bastion Servers are Crucial in IoT Infrastructure
IoT devices, while capable of transforming industries, are often vulnerable to attacks due to their limited processing power and lack of sophisticated security features. Cybercriminals exploit these weaknesses to inject malware, intercept data, or gain control of entire networks. This makes securing IoT infrastructure more challenging than traditional IT systems.
A bastion server addresses these risks by serving as the singular point of entry into a network of IoT devices. Instead of having direct internet exposure for each device, all remote access is funneled through the bastion server, significantly reducing the attack surface. The controlled access also makes it easier to monitor activity and detect unusual behavior.
Real-World Example
Consider a large-scale IoT deployment in an energy plant, where various sensors monitor and manage critical functions like temperature, pressure, and equipment health. These sensors often communicate with a central server, where data is processed and analyzed. A breach in this network could lead to catastrophic consequences. By using a bastion server, all external access to these systems is funneled through a single, highly secure node. This prevents unauthorized users from directly accessing these sensitive devices and creates an additional layer of defense against cyber-attacks.
Best Practices for Using Bastion Servers in Production IoT Environments
Least Privilege Access Control
Only authorized personnel should have access to the bastion server, and permissions should be limited to what’s necessary for their role. Implement multi-factor authentication (MFA) to protect against unauthorized access. In a production IoT environment, integrating MFA with SSH keys, password policies, and time-based one-time passwords (TOTP) is essential to reduce the risk of credential-based attacks. For example, energy companies often use MFA to ensure only authorized personnel can access IoT sensors and control systems.
Regular Updates
Keeping your bastion server’s software up-to-date is critical for defending against known vulnerabilities. Automated patch management systems can help streamline this process, ensuring that the server is always running the latest version of its operating system, security protocols, and software components.
Network Segmentation
By dividing the network into distinct segments (such as a DMZ and internal zones), bastion servers help isolate critical IoT systems from external threats. This limits lateral movement if one part of the network is breached. For example, in smart manufacturing, where multiple IoT devices handle sensitive data and control production, segmentation prevents attackers from accessing the entire infrastructure via a single compromised device.
Logging and Monitoring
All activities on the bastion server should be logged. Implement continuous monitoring tools to detect suspicious behavior. For example, any unexpected logins or attempts to escalate privileges should trigger immediate alerts.
Use of Encryption
Use end-to-end encryption protocols (such as TLS or SSH) for all communication between the bastion server and IoT devices. This ensures that even if the network is compromised, the transmitted data remains secure. This is particularly important in healthcare IoT deployments, where medical devices transmit patient data to central systems for analysis.
Backup and Failover Planning
Bastion servers should be part of a failover architecture. In case one server is compromised or taken offline, a backup bastion should be ready to take over, ensuring uninterrupted access and security.
Benefits of Using Bastion Servers in IoT Infrastructure
Enhanced Security
Bastion servers significantly reduce the attack surface by acting as a single, fortified gateway to sensitive IoT devices. This centralized security model strengthens defenses and enables better oversight.
Compliance
Many regulatory frameworks, such as GDPR and HIPAA, require robust security controls over data access and transmission. A bastion server helps ensure compliance by restricting and monitoring access to IoT networks.
Conclusion
As IoT continues to transform industries, securing these devices against cyber threats becomes critical to maintaining reliable and efficient operations. Bastion servers are a cornerstone of secure IoT infrastructure, providing centralized control, advanced monitoring, and reducing the attack surface. For any organization working with IoT, implementing a bastion server is a proactive measure that strengthens network defenses while improving scalability and compliance.
At 2Smart, we have extensive experience in deploying bastion servers to safeguard our platform and services, ensuring secure access control for our white-label instances. By sharing our knowledge and best practices, we aim to help other organizations enhance their IoT security and stay ahead of emerging threats.
Don't forget to share this post!
Read Next
Let’s dive into your case
Share with us your business idea and expectations about the software or additional services.